Shortly after posting The Demise of Firmware Passwords on M1 Macs, which I at least in part agreed with Apple’s assessment of FileVault being an equivalent level of security (so long as your users aren’t admins), someone commented on the fact that hidden in the menubar of the Recovery Assistant is an Erase Mac option!

From there, all it takes is a couple of extra clicks to begin erasing the entire system, including the main OS.

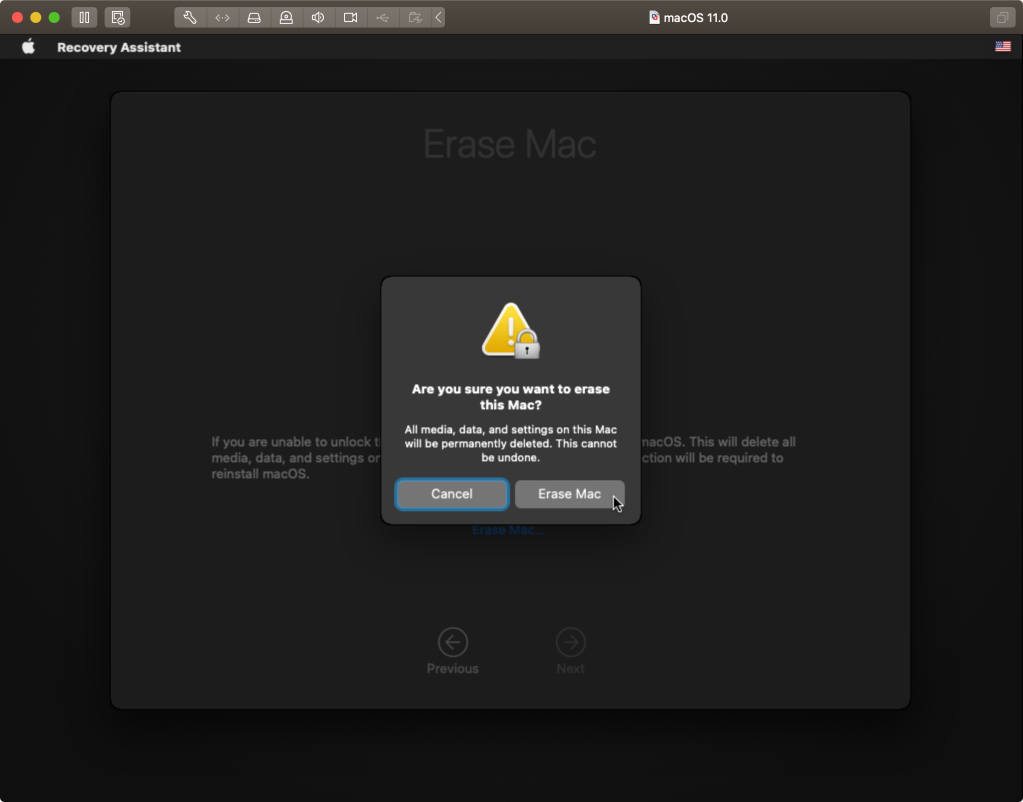
From an admin standpoint, this is very very bad… While your M1 Mac data may not be at risk of being exfiltrated or recovered, this means that Mac admins unequivocally do not have any greater control over the Mac hardware we purchase, deploy, and manage as anyone (literally anyone) who happens to be in physical possession of the hardware.


Does this mean that the AppleID or MDM/DEP then kicks in and only allows them to reinstall or reconfigure according to the prior AppleID MDM/DEP configuration? Or does the “possession is 9/10ths of the law” premise takeover and they can do whatever they want?
LikeLike
I haven’t gotten that far, but I have to imagine the AppleID or MDM/DEP kicks in (so long as it has an Internet connection)
LikeLike
If the M1 Mac is enrolled in DEP, then an erase will *require* activation via a working internet connection…which will re-enroll the MDM via DEP. So, that’s something.
LikeLike